Home > News >[Menlo Security] Magic Quadrant for Secure Web Gateways
News
2018-12-04
[Menlo Security] Magic Quadrant for Secure Web Gateways

Market Definition/Description
The market for cloud-based secure web gateway (SWG) services continues to grow more quickly than the market for appliance-based SWGs. (The five-year compound annual growth rate [CAGR] for SWG cloud services is 32%, and the five-year CAGR for SWG appliances is 5%.) However, in 2017, more money was spent to purchase SWG appliances (74% of market revenue) than SWG cloud services (26%).
The primary driver for the growth of SWG cloud services is the rapid adoption of software as a service (SaaS) applications, particularly the dominant ones (e.g., Office 365 and Salesforce). Rather than backhaul web traffic over expensive Multiprotocol Label Switching (MPLS) connections, enterprises are implementing local internet breakouts from remote offices, and sending web traffic directly to the internet. This approach mandates a change to the enterprise’s security architecture, and most are choosing to adopt a cloud-based SWG service. A distant secondary driver for the adoption of these services is the need to protect mobile users when they are off the corporate network.
Cloud access security brokers (CASBs) have emerged as an adjacent market to SWG (“Magic Quadrant for Cloud Access Security Brokers”). SWGs provide visibility into users’ web behavior, and CASBs provide visibility into users’ SaaS application behavior (for example, the SaaS applications they’ve visited and the risk rating of those apps). Many of the vendors in this Magic Quadrant have acquired CASB vendors, including Symantec (Blue Coat acquired Elastica and Perspecsys), Cisco (CloudLock), McAfee (Skyhigh Networks) and Forcepoint (SkyFence). Others, including Zscaler and iboss, have partnerships with Microsoft and its Cloud App Security CASB. In 2018, CASB vendor Netskope added basic SWG functionality to its cloud service. Gartner believes that the SaaS application visibility (and other functions) provided by CASB is an important element of web security, and we emphasized CASB capabilities more heavily in our Completeness of Vision scores this year.
Gartner has continued to monitor the impact of the remote browser isolation solutions on the SWG marketplace. These solutions render the image of a website in the cloud or on an appliance in the customer’s data center, and send this image to a user’s browser. This technique protects endpoints from typical web threats by executing and rendering all content remotely. Ideally, no malicious content is ever rendered by the user’s browser, and web interaction can be tightly controlled.
This year, Menlo Security, the largest of the pure-play remote browser isolation vendors qualified for inclusion in this Magic Quadrant. We are also closely tracking Cyberinc and other vendors in this market. In July 2017, Symantec acquired Fireglass, another remote browser isolation vendor, and it now offers this capability as a feature of its SWG.
Another emerging market Gartner is closely tracking is cloud-based firewalls. Vendors in this market base their underlying technology on cloud firewalls and offer security stacks, including URL filtering, sandboxing and other functions. Vendors in this category include Cato Networks, OPAQ, CenturyLink (Level 3 Communications and its Adaptive Network Security service), and Palo Alto Networks (GlobalProtect Cloud Service). Gartner primarily sees these services in the midmarket, and their feature sets position them to compete against SWG vendors.
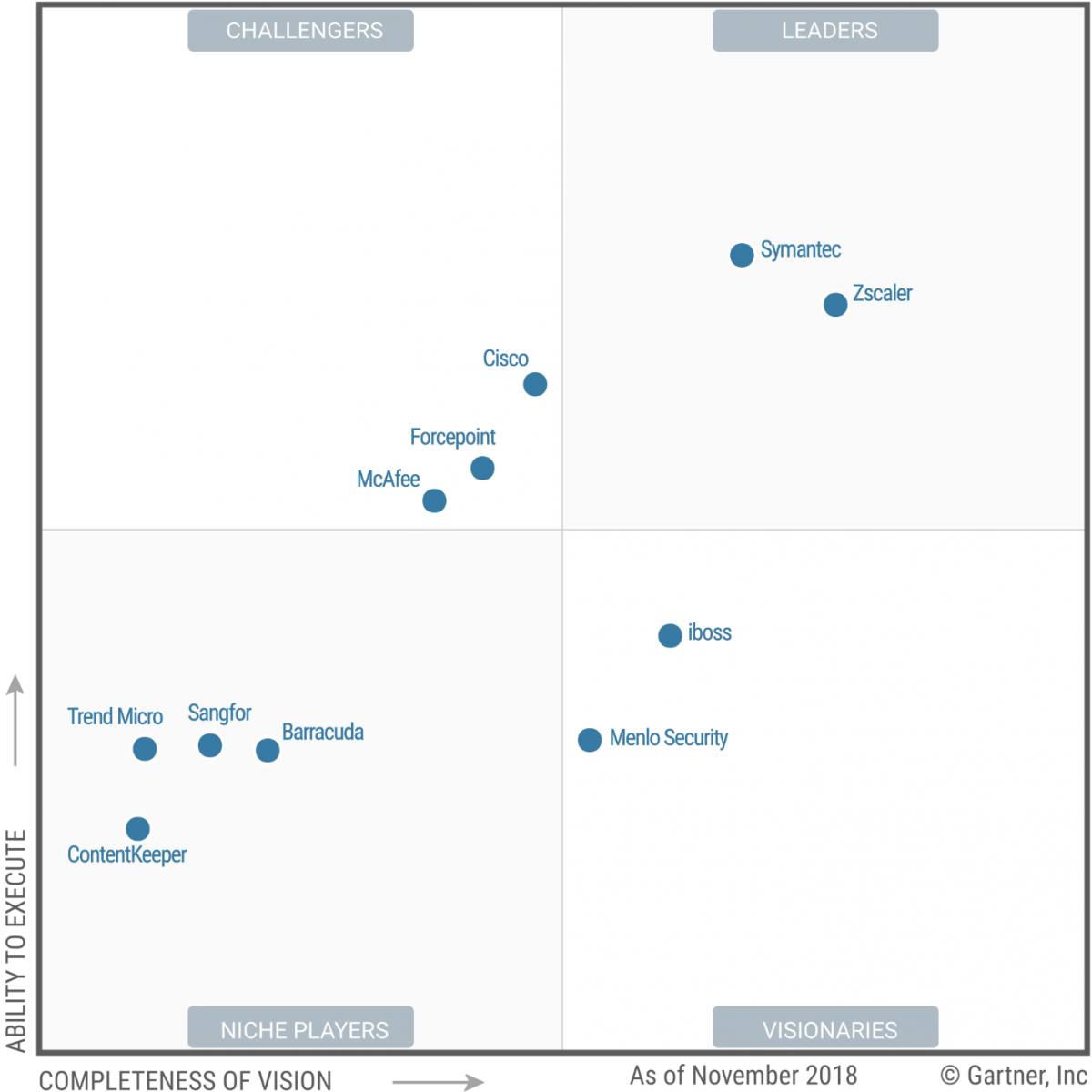
Magic Quadrant
Figure 1. Magic Quadrant for Secure Web Gateways

Menlo Security
Based in Palo Alto, California, Menlo Security is a new entrant this year. It provides an isolation-based SWG platform, and its new architectural approach executes webpages on isolated browsers and mirrors the rendering to the end user’s machine. The dual-engine approach uses the browser’s Document Object Model (DOM) with Adaptive Clientless Rendering (ACR) or Pixel ACR to ensure an optimal user experience. This eliminates malicious drive-by attacks and provides techniques that minimize the risk of downloaded files and password theft. The isolation-based solution can be delivered on-premises or from the AWS cloud (more than 95% of Menlo’s customers use the cloud service). Menlo has several large-scale, global-enterprise deployments and is a good choice for enterprises with a high priority on security.
Strengths
-
The Menlo Security Isolation Platform (MSIP) is a proactive way to protect endpoint devices from browser vulnerabilities, JavaScript redirects, Flash vulnerabilities and font/image vulnerabilities by rendering mirrored or transformed content to the user’s local browser.
-
Menlo licenses Webroot’s URL classification database. Administrators can create and store compound searches and reports using Menlo’s Insights analytics engine, and Menlo further provides an API for SIEM integration.
-
If policy allows users to download content, executable files can be inspected by the Menlo sandbox (the OEM provider is Sophos). They can also leverage customers’ Palo Alto Networks Wildfire and FireEye sandboxes already deployed, while documents can be converted into safe HTML/PDF files for local storage. Encrypted content, including TLS/SSL, is already decrypted in the cloud browser, which eases content inspection.
-
Flexible policy for web traffic can restrict file downloads and web write privileges, enforce corporate-certified browsers and block nonbrowser traffic, such as command and control. Menlo’s “Vulnerable Services” category dynamically classifies websites using vulnerable applications, such as WordPress 4.8 or Drupal 7, enabling policy isolation for this content.
-
Menlo isolates email links and web mail to protect against malware and thwart spear-phishing attacks. It also actively warns users at “time of click” to prevent credential theft.
Cautions
-
Menlo is an emerging vendor that’s less mature than larger competitors. It has received more than $85 million in financing, and is growing rapidly; however, it is not yet cash-flow-positive.
-
The cloud service is delivered on AWS, and is thus restricted to Amazon’s geographic presence. Local off ramps are available to ensure the delivery of localized content, present sites in the appropriate language and deliver a transparent local experience.
-
Menlo does not offer CASB or native DLP functionality.
-
Laptops are connected via VPN or less secure proxy auto-configuration (PAC) files only. Menlo does not offer a local agent, but plans to by year-end 2018. Although it supports other traffic redirection methods, such as IPsec tunnels from remote offices, most of Menlo’s customers use PAC files.
Sangfor
Based in China, Sangfor has two primary business units: network security and cloud computing. Within network security, SWG represents about half of its revenue. The remaining revenue in the network security business unit comes from its next-generation firewall (NGFW), VPN, WAN optimization controller (WOC), ADC and endpoint security products. Sangfor’s SWG is named Internet Access Management (IAM). It comes in a hardware appliance form factor or as a virtual appliance, and it is implemented as an in-line transparent bridge. In 2018, the company introduced an SWG cloud service.
In 2017 and 2018, it has also added Sangfor Engine Zero, an artificial intelligence (AI)-based malware inspection engine; Neural-X, a threat intelligence and traffic/flow-based analysis for botnets; and ZSand, a sandbox for malware detection. Nearly all of the vendor’s revenue is generated in the APAC region. Sangfor is a strong candidate for organizations based in China and other supported countries in the APAC region.
Strengths
-
Sangfor has strong application control features. It can apply granular policies to microblogging services, Facebook and other web-based applications, and it also has developed network signatures based on traffic patterns to block port-evasive applications, such as BitTorrent and Skype. Due to its localized application database, Sangfor’s application and URL visibility and control are particularly strong for the Asian market.
-
The vendor’s in-line transparent bridge mode enables flexible and granular bandwidth control capabilities. Bandwidth utilization parameters can be specified for uplink and downlink traffic. This is an important feature in the APAC region, where bandwidth costs are high.
-
Sangfor applies analytical techniques against the data it captures from user traffic. Customers can implement embedded apps, such as a UEBA feature that monitors the risky behaviors of users or Internet of Things (IoT) devices on the network. Third-party apps can access Sangfor’s data through APIs. Sangfor offers a unique feature that reports on wasted electricity (electricity is expensive in China).